
A new malware framework recognised as NetDooka has been uncovered currently being distributed via the PrivateLoader pay back-per-put in (PPI) malware distribution provider, permitting risk actors entire accessibility to an contaminated machine.
This formerly undocumented malware framework characteristics a loader, a dropper, a protection driver, and a impressive RAT ingredient that depends on a custom community communication protocol.
The very first samples of NetDooka had been discovered by scientists at TrendMicro, who warn that even though the resource is nevertheless in an early advancement stage, it is previously extremely capable.
The fact that it is becoming distributed through the PrivateLoader malware distribution service displays this efficiency, as its authors considered the malware completely ready for substantial-scale deployment.
PrivateLoader deployment
The PrivateLoader PPI assistance was initially spotted a year back and analyzed by Intel471 in February 2022. In short, it is a malware distribution platform that depends on Website positioning poisoning and laced documents uploaded on to torrent web-sites.
It has been observed distributing a vast range of malware, like Raccoon Stealer, Redline, Smokeloader, Vidar, Mars stealer, Trickbot, Danabot, Remcos, and numerous other malware strains.
TrendMicro analysts spotted NetDooka taking in excess of handle of the an infection chain immediately after being dropped on the victim’s device in recent operations.
Very first, a loader is decrypted and executed, examining the Home windows Registry for the existence of antivirus tools that will be taken off or disabled.
Up coming, a destructive set of motorists is mounted to act as kernel-method defense for the RAT component, blocking the deletion of the payload or the termination of its procedures.
Eventually, the framework establishes a communications link to C2 for fetching the ultimate payload, the NetDooka RAT. Pattern Micro notes that in some cases, PrivateLoader drops the RAT immediately.
.jpg)
NetDooka RAT
In advance of moving into regular operation manner, NetDooka RAT checks if it is working in an assessment ecosystem and if a duplicate of by itself presently exists on the procedure.
The RAT gets commands through TCP and supports a range of functions like performing file actions, logging keystrokes, executing shell commands, working with the host’s methods for DDoS assaults, or doing remote desktop operations.
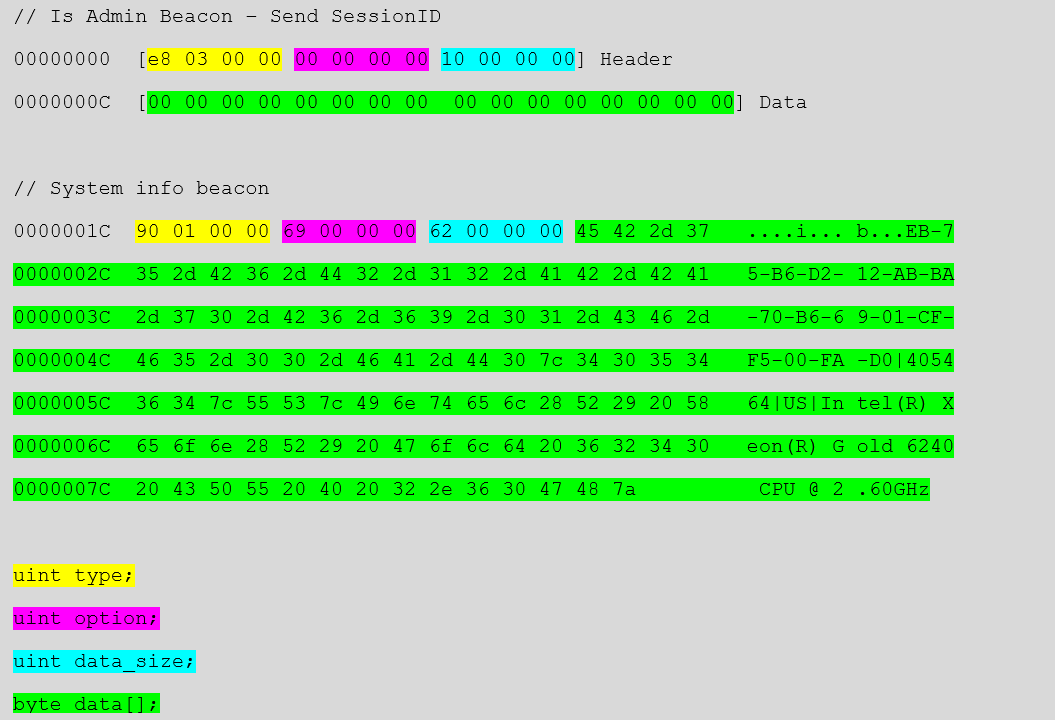
The finish list of supported capabilities is offered below:
- Exfiltrate procedure info
- Deliver session ID
- Deliver message
- Reverse shell
- DDoS assault
- Send out file
- Download file
- Copy browser facts
- Duplicate browser info
- Start HVNC
- Deliver log
- Microphone seize
- Begin virtual community computing (VNC)
- Capture webcam
The communication between C2 and NetDooka RAT relies on a tailor made protocol, with the exchanged packets resembling the subsequent structure:
Because NetDooka is in an early advancement phase, any of the over may possibly alter quickly, and there are presently variants circulating that element distinct operate sets.
Suitable now, it is a device that menace actors could use to create shorter-time period persistence and conduct data stealing and espionage functions.
However, considering the fact that it incorporates a loader as section of the malware frame, it could fetch other malware strains apart from its personal RAT part.



