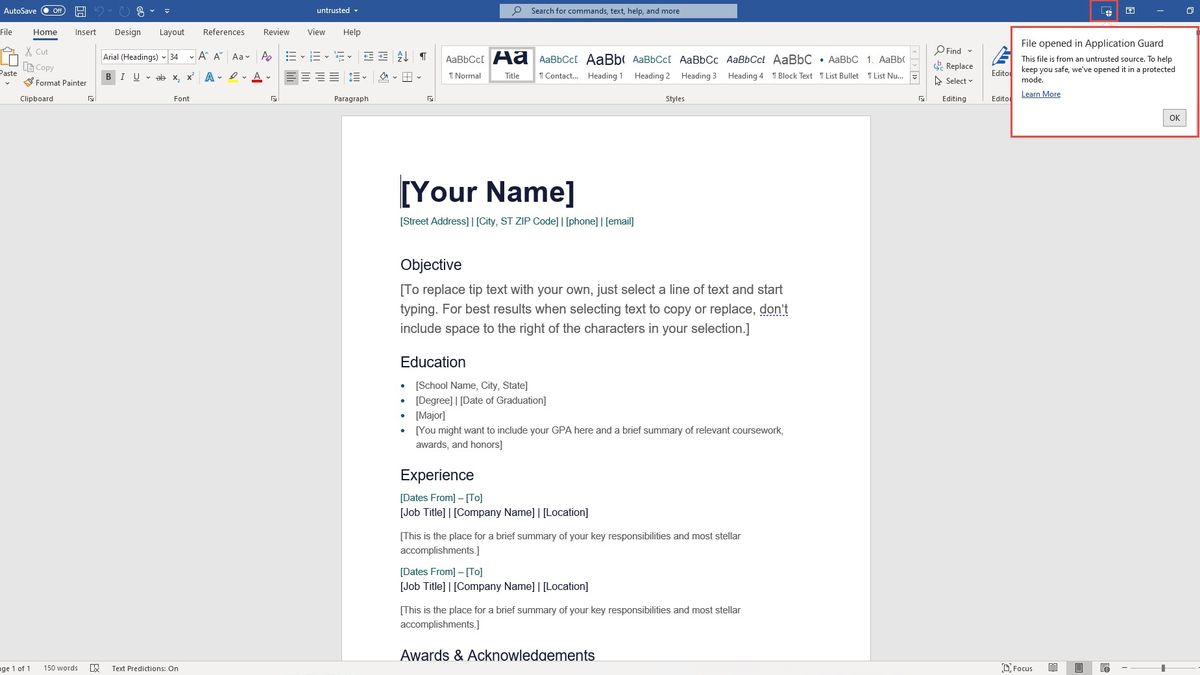
Malicious attachments are often used by cybercriminals as a means to gain access to an organization’s network...
clever
As more businesses shift their workloads to cloud environments, Linux threats are becoming increasingly common and cybercriminals...